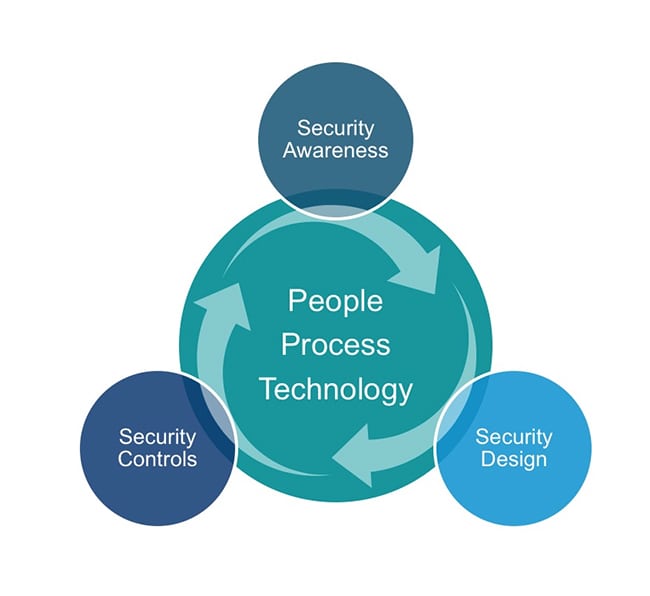
SECURE BY DESIGN
Modern data security baked in, not bolted on
-
Comprehensive & centralized data security
Entrust your customer data to Syncari. Our platform includes a multitude of data policies such as PII data masking and encryption for data in transit and at rest that can be enforced across your entire tech stack. -

Industry & government compliance
Data privacy and protection are core to what we do. Our SOC 2 Type II, HIPAA, and support for GDPR/SCCs, CCPA, and Privacy Shield compliance validate our commitment to exceeding the level of security required by industry, state, and federal governments. -

Infrastructure security & resiliency
Built for the cloud, Syncari leverages the most sophisticated cloud security technologies available. The result is a platform that is secure and resilient, giving you the confidence to enable your most demanding data workloads with Syncari.